Although Microsoft Outlook is a popular business email client app, it’s not perfect. There are several common Outlook issues that users often experience while using it. These Outlook issues may not only disrupt the email communication but also result in loss of mailbox items due to damage to Outlook data file (OST/PST) or corruption. Thus, it’s critical to prevent and fix the common Outlook issues and avoid data loss. Stellar Repair for Outlook can easily make solutions to all the below issues.
In this article, we’ve discussed 10 common Outlook issues that can disrupt your business communication and lead to data loss, along with the fixes to quickly resolve them.
List of 10 Common Outlook Issues and their Solutions
Below we have compiled a list of 10 common Outlook issues that one may experience during everyday Outlook use. These include Outlook errors such as 0x800ccc0f, 0x80040154, 0x800CCC13, etc. You may resolve these common Outlook issues by following the solutions discussed below or use an Outlook repair software, such as Stellar Repair for Outlook. The software can help repair damaged or corrupt Outlook data file (PST) and resolve all kinds of Outlook issues in a few clicks, without the risk of data loss. It’s compatible with Outlook 2021, 2019, 2016, 2013, 2010, 2007, and 2003 versions.
1. Error 0x800ccc0f
The cryptic Outlook error code 0x800ccc0f appears while sending or receiving emails. The error may occur in MS Outlook 2021, 2019, 2016, 2013, 2010, and 2007 due to poor network connection, firewall settings, corrupt or oversized Outlook data file (OST/PST), etc.
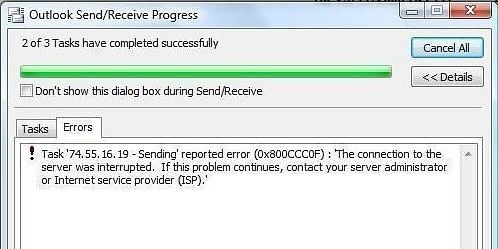
The error can be fixed by ensuring correct configuration settings in Outlook and a stable connection with the mail server. You may also disable your firewall settings or antivirus protection to check if the problem is caused by them. Further, you may also check the Outlook data file for errors or damage and repair it with the help of Inbox Repair tool or an Outlook repair software (as mentioned earlier) to fix the error 0x800ccc0f. The Outlook repair software can also help reduce the size of an oversized PST file by compressing it. This will resolve the issue if it is occurred due to an oversized Outlook data file.
2. Microsoft Outlook Has Stopped Working
MS Outlook may stop working or may not respond due to reasons, such as faulty add-ins, damaged or lost DLL files, corrupt Outlook profile, damaged Outlook program or Outlook data file, etc.
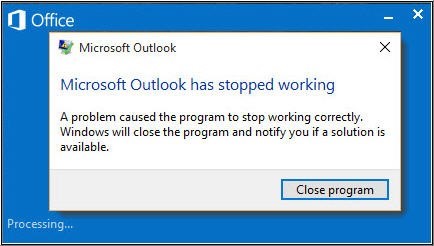
However, this Outlook issue can be resolved by removing faulty add-in(s), creating a new Outlook profile, reinstalling or repairing the Outlook program, or by repairing the damaged Outlook data file. To know more about this Outlook issue and fix it, refer to our guide on Microsoft Outlook Stopped Working.
3. Not Implemented Error
“Not implemented” is another Outlook send/receive error message that appears when a user clicks on the Send/Receive button to manually send or receive emails.
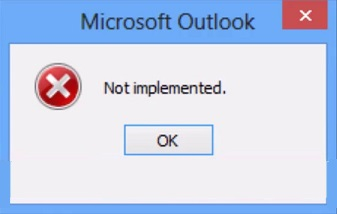
This send/receive error may occur due to faulty add-ins, incorrect configuration, damaged Outlook profile, or corrupt PST file. To fix this Outlook issue, you can refer to our in-depth guide on Fix “Not Implemented” Error in Microsoft Outlook on Windows.
4. Error 0x80040154
The error 0x80040154 is yet another Outlook error that appears when a user tries to send or receive emails. It occurs due to damaged Outlook program, incompatible software (antivirus program), faulty add-in, damaged or corrupt DLL files, ActiveX control issues, a problem with COM components, etc.
You can resolve this Outlook issue by reinstalling the Outlook, removing the faulty add-in, or using the Microsoft Support and Recovery Assistant utility. We have already discussed this error in detail and explained various solutions to fix Microsoft Outlook error 0x80040154 on Windows.
5. Error 0x800CCC13
The error 0x800CCC13 occurs due to connectivity issues, incompatible add-ins, virus or malware intrusion, bad sectors on the drive, etc.
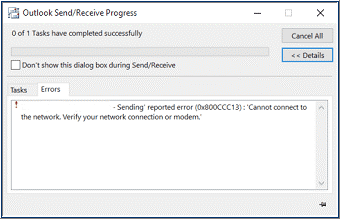
However, you can resolve this issue by checking the internet connection and running the SFC (System File Checker) scan on the system. However, if that does not work, follow this guide to resolve the error “0x800CCC13” Outlook cannot connect to Server.
6. Error 0x8004210A
The error 0x8004210a is a server timeout error that indicates a problem with Outlook’s send/receive functionality. The complete Outlook error message is as follows,
“Task ‘XXXX’ reported error (0x8004210A): ‘The operation timed out while waiting for a response from the receiving (POP) server. If you continue to receive this message, contact your server administrator or internet service provider (ISP).’
This error occurs due to incorrect settings, connectivity issues, and problems with Outlook data files. You can fix this by ensuring reliable internet connectivity, increasing the server timeout interval, etc. To know more about the solutions to resolve this error, follow How to Fix POP Server Timeout Error 0x8004210a in MS-Outlook or Send/Receive Pop Error.
7. Error 0x80040600
The error 0x80040600 is another send/receive error that occurs when an Outlook user tries to send, receive, or delete email messages. The error is usually caused by a large or oversized PST file that exceeds the mailbox size limit. It may also occur if the PST file is damaged or corrupt.
To resolve this issue in Outlook, you may attempt to compact the PST file or repair it via the ScanPST.exe utility. For more details and steps to resolve this Outlook issue, follow our guide on How to Fix ‘An unknown error has occurred 0x80040600’ in MS Outlook.
8. Outlook Search not Working
Microsoft Outlook has a search option that allows users to find emails based on keywords. It also provides several filters to quickly locate specific email or mail items. However, sometimes, this search option may fail or not list any results.
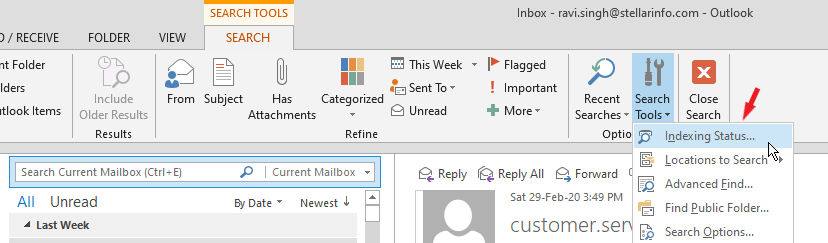
This may occur due to problems with Outlook indexing, problematic add-in, or issue with the Windows search service. To resolve this Outlook issue, you can follow our comprehensive guide on How to Fix Outlook Search When Not Working.
9. Microsoft Outlook Not Responding Error
Outlook not responding or Outlook not working is a common Outlook issue where Outlook application gets stuck or freezes. This may occur due to outdated system drivers, virus or malware intrusion, lack of system resources, or system overheating. It may also occur if the Outlook data file is damaged.
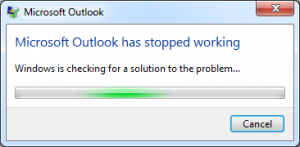
To resolve this, you may free up more resources by closing other applications, update Outlook and Windows, uninstall incompatible or faulty add-ins, etc. For a detailed guide, visit How to Deal with ‘Microsoft Outlook Not Responding’ Error.
10. Outlook Performance Issue
Usually, Outlook works without any hiccups on compatible systems. However, as the size of Outlook data file i.e., PST reaches or exceeds the mailbox size limit, Outlook performance starts to drop significantly. This can lead to issues such as delays in sending or receiving emails, integrity issues, PST file errors, and corruption.

However, this issue can be resolved by splitting the PST file into smaller sizes and by storing the Outlook data file on system drive or volume rather than on network storage. To know more about Outlook performance issues and how to resolve them, refer to our previous post Fix Outlook Slow in Outlook 2021, 2019, 2016, 2013 & earlier versions.
Conclusion:
In this article, we’ve covered 10 common Outlook issues and their solutions to help you troubleshoot and resolve these issues. However, there are several other not so common Outlook issues that we haven’t covered in this post. In case you have encountered a different Outlook error than what we’ve covered in this article, you can always use an Outlook repair software as discussed in this post to fix the error without the risk of data loss. You may also reach us and let us know the Outlook error you’re facing it via comments down below. We will try to get back to you with the best solution possible.
![Outlook Send/Receive Error 0x8004010F[Solved] Outlook Send/Receive Error 0x8004010F[Solved]](https://technixguru.com/wp-content/uploads/2024/03/How-to-fix-outlook-error-768x378.png)